Consul 1.16, the latest version of Hashicorp's service mesh tool, has been released. This release contains many enhancements that improve service mesh reliability, user experience, and security.
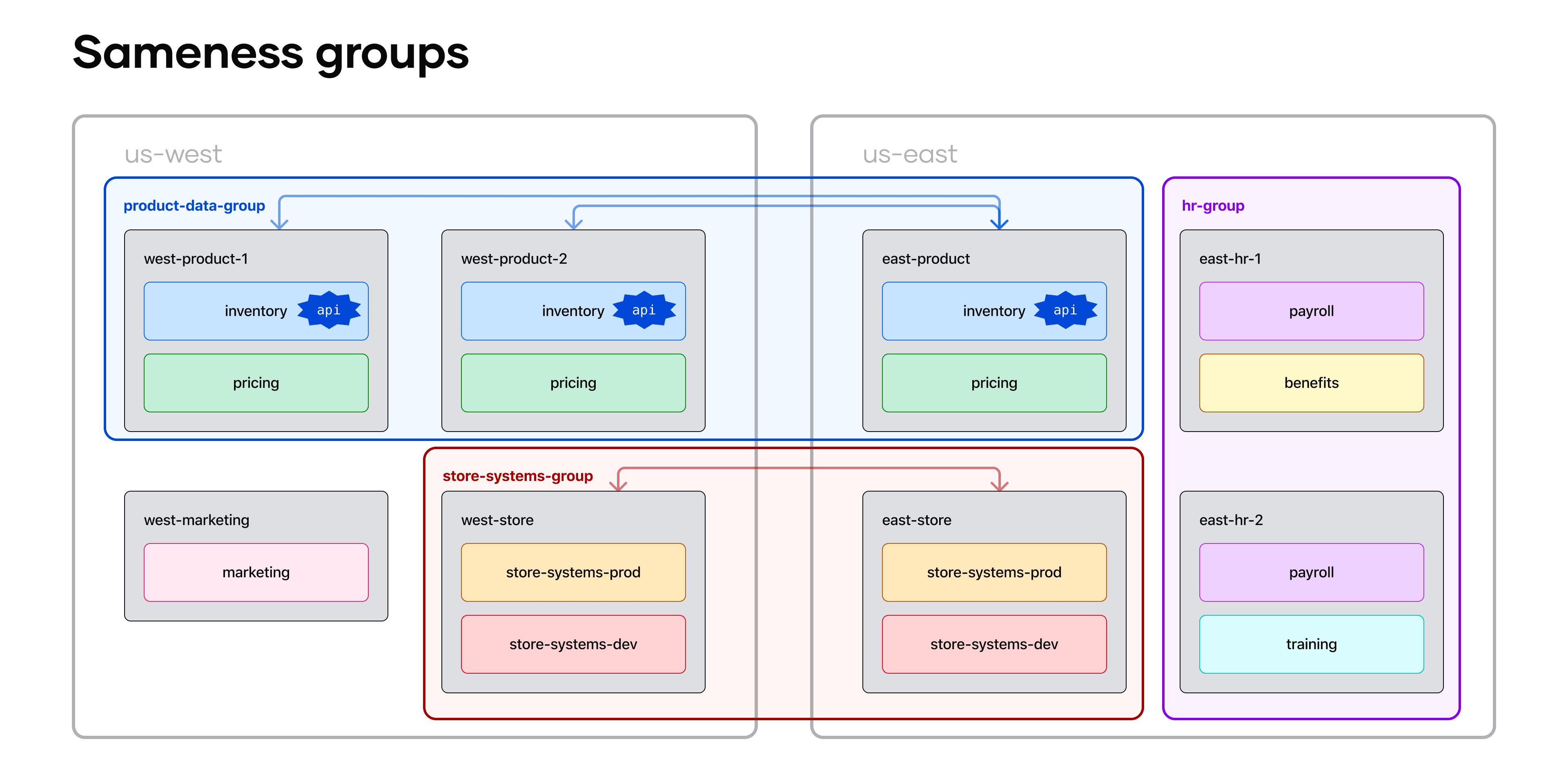
"Sameness Groups" have been introduced as a beta feature in Consul Enterprise to improve reliability and scalability, allowing seamless failover handling between active-standby clusters under common administration. Sameness Groups allow administrators to group Consul peers and partitions logically, facilitating efficient failover should there be an issue in a particular cluster or region to an equivalent standby cluster without interrupting service.
In Consul Enterprise, Control plane protection has been enhanced with per-IP rate limits, providing better control over resource utilization and preventing resource exhaustion and service disruptions by allowing administrators to control and limit requests based on their source IP address.
For security concerns in regulated environments, Consul Enterprise now offers FIPS 140-2 compliant builds, meeting security requirements for federal agencies by using a certified cryptographic module and specific safeguards to comply with Level 1 requirements.
JWT authentication for service-to-service traffic is now possible, authorizing connections based on claims in JSON Web Tokens. This allows administrators to offload JWT validation to Consul, providing a uniform method for authorized communication between services.
Service Mesh user experience has been improved. The transparent proxy mode now supports failover between service instances deployed across clusters and routing to virtual services, providing operational simplicity for cross-cluster failover. In prior versions of Consul, this was operationally complex, but this now works seamlessly by transparently routing traffic to a backup service. The transparent proxy also now supports virtual services without explicit configuration.
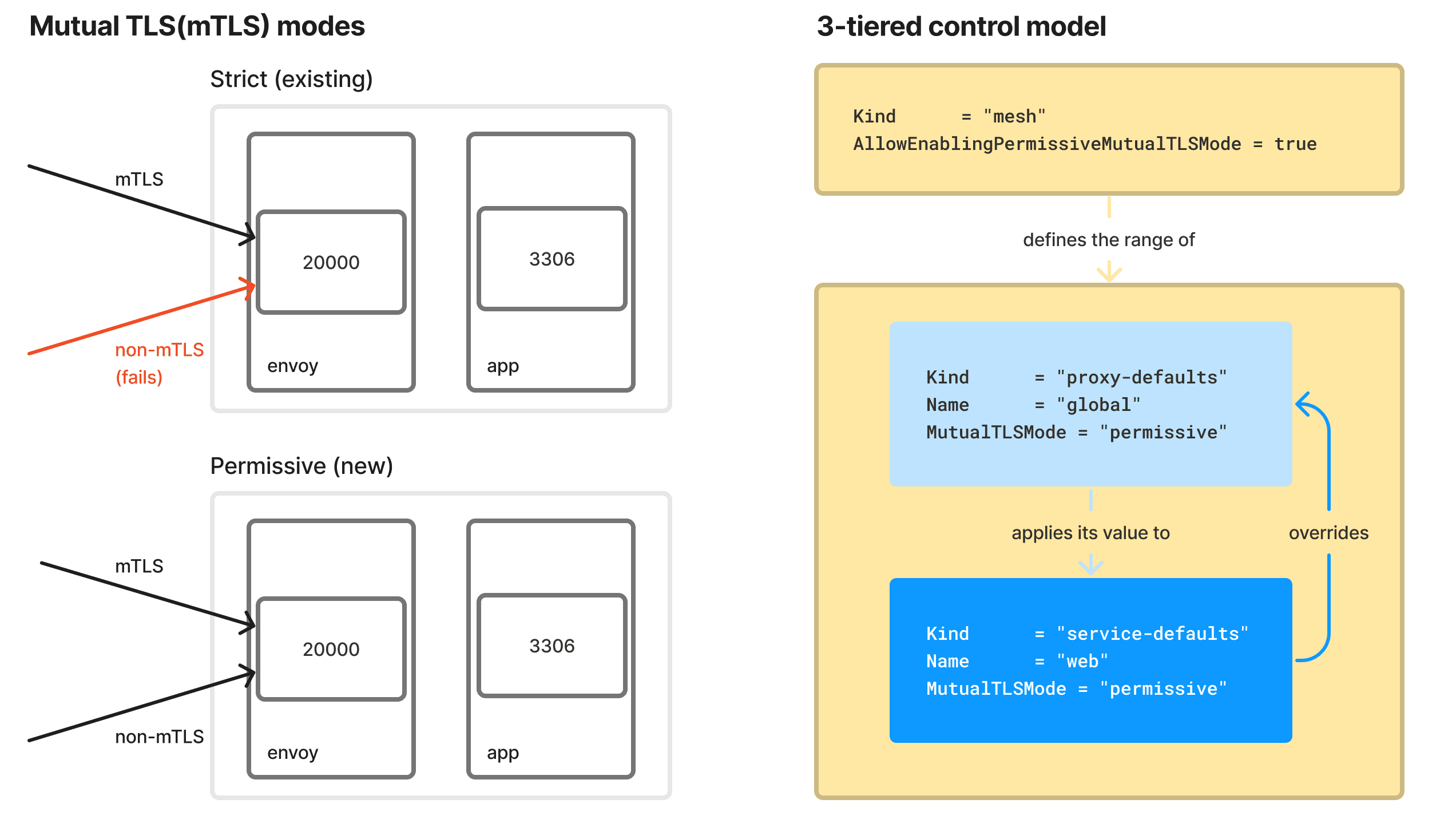
Permissive mTLS is now enabled to allow gradual onboarding of services to the service mesh while maintaining connectivity with external downstream applications. This allows upstream services to accept mTLS traffic secured through Consul's service mesh and traffic from external downstream applications not yet managed by Consul.
Several extensions for Envoy Proxy have been added. Firstly, an external Authorization Envoy extension for augmenting Consul's service intentions with custom authorization solutions. Next, a property override extension allows administrators to fine-tune their Envoy configuration from within Consul configuration entries. Finally, a WebAssembly (Wasm) Envoy extension allows custom WebAssembly plugins on TCP and HTTP listeners per-service or mesh-wide.
In Service Discovery, catalog sync now supports health checks and ingress resources. This means that Kubernetes pod health status is directly linked to service instances, which improves traffic routing and provides a more comprehensive and integrated view of Kubernetes resources within Consul.
Interested readers can learn more about Consul 1.16 in the HashiCorp launch blog post.