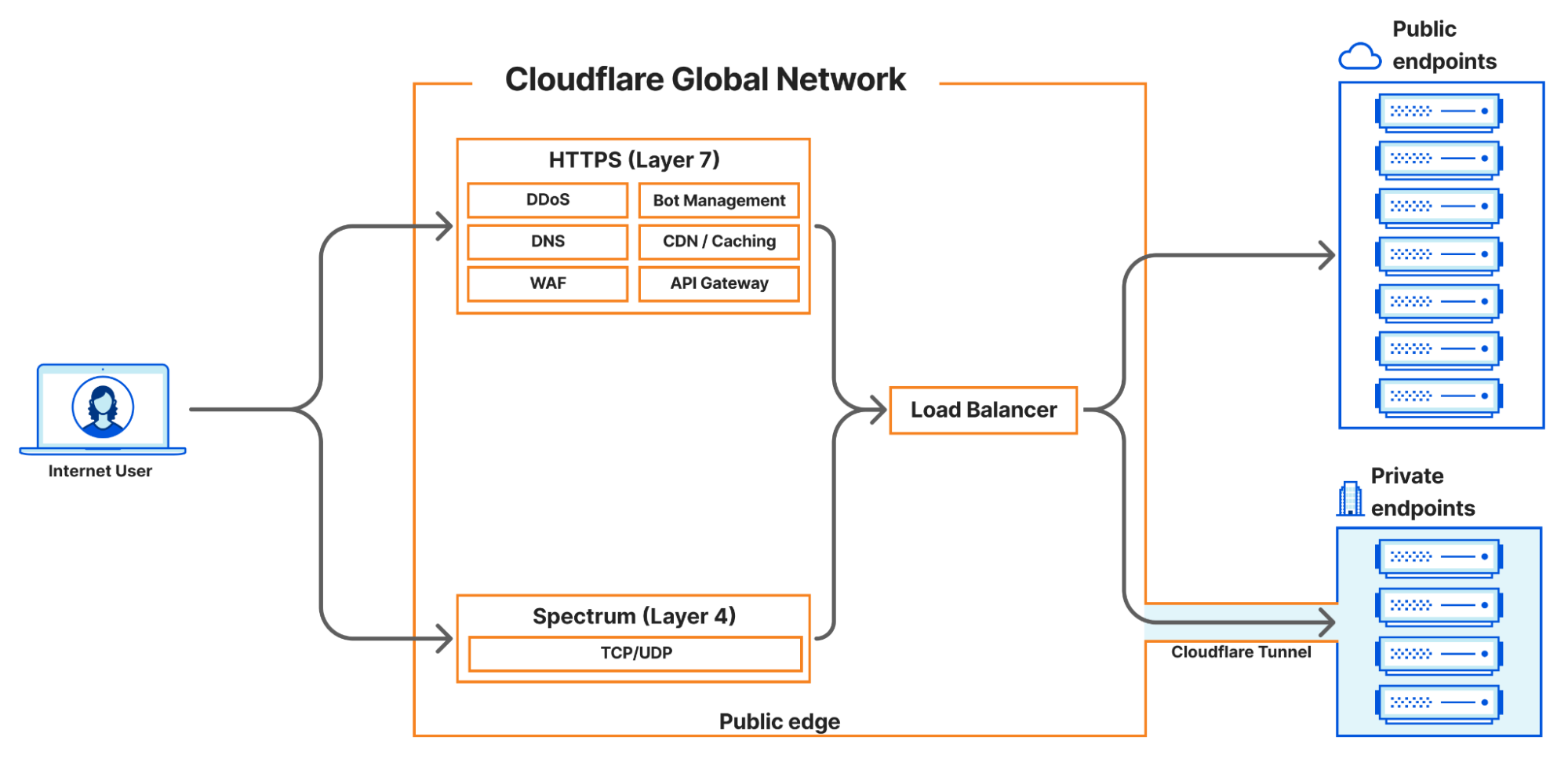
Cloudflare recently unveiled significant advancements in its load balancing capabilities, aiming to eliminate the need for hardware-based solutions. The company’s latest enhancements integrate seamlessly with Cloudflare One, providing end-to-end private traffic flow support and WARP authenticated device traffic. This development allows organizations to balance public and private traffic directed at privately hosted applications without needing dedicated hardware load balancers.
Cloudflare’s existing solution supports layer 4 load balancing for TCP and UDP traffic within private networks through Spectrum (a layer 4 reverse proxy that protects against DDoS attacks and conceals a customer’s private origin IP address, preventing direct attacks) and layer 7 load balancing via Cloudflare tunnels, which allows organizations to balance public HTTP(S) and private traffic, offering a load balancing solution for all network types.
(Source: Cloudflare blog post)
Earlier, Cloudflare’s layer 4 load balancers were connected to the public Internet. Although customers could secure that traffic with WAF rules and Zero Trust policies, some preferred to keep resources private. Isolation for layer 4 load balancers is now available for origin servers and endpoints.
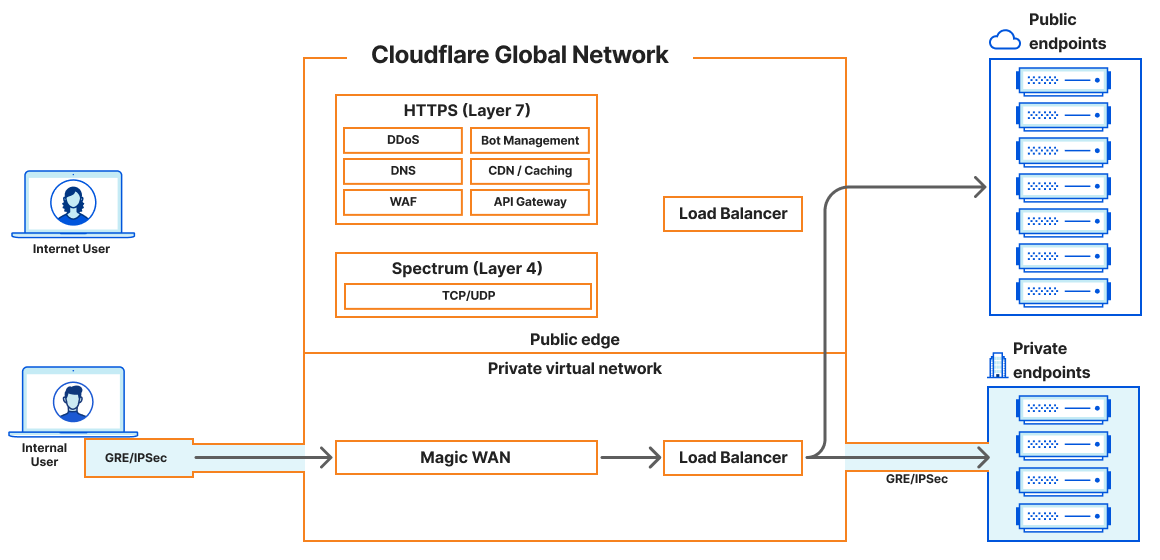
Moreover, load balancers accessible at private IPs can now be utilized within a virtual network to segregate traffic to specific sets of Cloudflare tunnels. This allows customers to balance traffic within their private network without exposing their applications to the public internet.
Also, Cloudflare Magic WAN can now be used as an on-ramp with Cloudflare load balancers accessed via a private IP address, providing a secure, high-performance connection to internal resources and ensuring private and optimized traffic across the global network. Customers can connect their corporate networks directly to Cloudflare's network with GRE or IPSec tunnels, maintaining privacy and security.
(Source: Cloudflare blog post)
The enhancement enables various internal load balancing use cases, including managing traffic between data centers, routing traffic for internally hosted applications, optimizing resource allocation for critical applications, and ensuring high availability for internal services.
Noah Crouch, a product manager at Cloudflare, writes:
Organizations can now replace traditional hardware-based load balancers, reducing complexity and lowering costs associated with maintaining physical infrastructure. By leveraging Cloudflare load balancing and Magic WAN, companies can achieve greater flexibility and scalability, adapting quickly to changing network demands without the need for additional hardware investments.
Lastly, Cloudflare WARP can now reach Cloudflare load balancers with private IP addresses. The WARP client protects corporate devices by securely and privately sending traffic to Cloudflare's global network. It also allows advanced web filtering through Cloudflare Gateway and enables advanced Zero Trust policies to check a device's health before connecting to corporate applications.
With Cloudflare enhancing its load balancing product and eliminating hardware, other load balancing solutions are available to provide high availability, scalability, and performance without needing dedicated hardware. For instance, AWS offers Elastic Load Balancing, which automatically distributes incoming application traffic across multiple targets, such as Amazon EC2 instances, containers, IP addresses, and Lambda functions, or VMware NSX Advanced Load Balancer, which provides multi-cloud load balancing, web application firewall, application analytics, and container ingress services across on-premises data centers and any cloud. In addition, another example is F5 NGINX Plus, a software load balancer, web server, and content cache built on top of open-source NGINX - which adds several features to its open-source counterpart, including active health checks, session persistence, and more.